The
GroupWise Skeleton Key (
GWSK ) allows an
authorized individual to access the contents of
any mailbox in your GroupWise 6.5 or higher system. It is the
ideal tool for performing the sad and sorry task of snooping ( auditing,
discovery, spying, whatever euphemism you choose to use ) in employee's
mail under the direction of executive management.
Details
The package consists of two pieces:
GWSK Manager
and
GWSK Proxy. The GWSK Manager is simple
Windows GUI tool for GroupWise administrators to manage GroupWise Trusted
Application Keys. GWSK Manager allows you to create and delete
these keys and creates encoded credentials used by GWSK Proxy.
GWSK Proxy a cross platform IMAP proxy written in Java.
It allows you to use the credentials created with GWSK Manager
to access any user's mailbox on your GroupWise 6.5 system using an
IMAP client like Thunderbird, Netscape Mail, etc. GWSK Proxy can
be run on any OS platform supporting JRE 1.3.1 or higher. When
your IMAP client connects to GWSK Proxy, the proxy authenticates with
the GroupWise IMAP server using the using the special trusted application
credentials. And of course GWSKProxy supports IMAP via SSL connections
to your GroupWise IMAP server - so you can safely use it from anywhere.
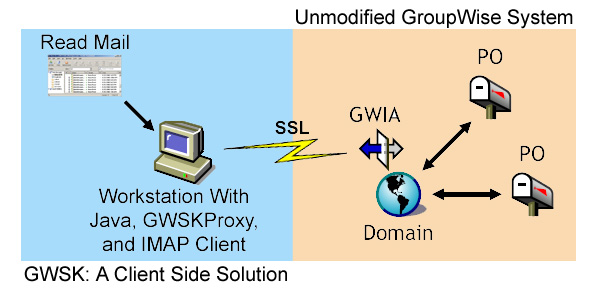
[ With GWSK, you never install software on your servers! ]
You use any IMAP client capable of handling null passwords.
We recommend the use of Mozilla Thunderbird or Netscape Mail. So
virtually any workstation with any OS can be used. Since the
GWSK Proxy provides an IMAP4rev1 connection, it works with a large number
of 3rd party IMAP utilities, scripts, and so on including IMAPCopy for
bulk duplication of user's mailboxes.
Minimum System Requirements
- GroupWise 6.5 or 7.0, preferably patched, with IMAP
access enabled for users's mailboxes to be examined.
- Key Generation Station: Windows 2000 or XP workstation
*
with admin rights over the primary GroupWise domain.
- Mailbox Audit Station: Linux, Mac, Unix, or Windows
*
with Sun Java JRE 1.3.1 or higher, and an IMAP client
- The IMAP client must support null passwords: Thunderbird,
Netscape Mail, etc. Eudora does not.
* Neither needs to be dedicated to this function. The Windows 2000
/ XP workstation is required only to set up a trusted application key.
This is done infrequently. Once a key has been generated,
it can be used from a Linux, Mac, Unix, Windows, etc. platform to review
user's mailbox contents. Both applications are relatively small and
do not require additional disk space, RAM, or other resources
System Recommendations
- Your GroupWise 6.5 system should be patched to GW 6.5
SP 2 or better.
- You use GWSK Proxy with the free Mozilla Thunderbird
E-Mail Client from a Windows workstation.
- To use IMAP over SSL, please use Sun JRE 1.4.1 or higher
to ensure a current version of JSSE is installed.
- IMAP over SSL is recommended to ensure security when
using GWSK over an internet connection
Since GWSK Proxy runs on any platform with a JRE, numerous other platform
are supported. However the IMAP clients on these platforms may
provide more or less features. To use SSL to connect to your GroupWise
server, please use Sun JRE 1.4.1 or higher to ensure a current version
of JSSE is included. GWSK should operate with SSL properly under
JRE 1.3.1 + JSSE 1.0.3 installed. If using GWSK to inspect mail from
a remote site, please configure GroupWise to accept IMAP over SSL connections
and use the GWSK -ssl startup option.
Purchasing
No educational discount nor non-profit discount is available on this product
as it has no legitimate use except in managing employee's mailboxes. GWSK
is licensed per end-user site, where a site consists of all GroupWise systems
operated by a particular end-user entity. If used by a consultant,
VAR, system integrator, or IT oursourcing agency, a separate and distinct
license MUST be purchased for that customer's site.
The GWSK costs $249 USD.
Purchase via our SW-REG store.
FAQ
Q: What is the difference between GWSK and offerings
from Nexic or GWAVA?
A: GWSK is a simple tool that does one thing well: examine a GroupWise
mailbox without its password. GWAVA and Nexic solutions do this and
perform many other features. They cost a lot more, and unless you
really need these features you are wasting money. Compare features
carefully, and choose a package that fits your needs.
Q: I already have a Nexic or GWAVA solution, why would
I buy yours too?
A: Even if you have a heavy weight tool in place, GWSK is still a
good fit for many places. GWSK is a lightweight solution, and does
not require any software to be installed on the server. It is the
only cross platform solution: Mac, Linux, Windows. GWSK is the only
solution that can be securely used over the Internet, from a wireless internet
connection in an airport, or even a public access workstation.
Q: In what ways, if any, is GWSK "better" than these
other products?
A: Well, GWSK doesn't do a lot of the things these other products do,
so its not a fair comparison. GWSK
does not require
any invasive software to be installed on your GroupWise server. There
are no NLM's, agents, or other things that might destabilize your GroupWise
system. GWSK uses your existing GroupWise system's IMAP capabilities,
and you use a standard IMAP e-mail client.
Q: I already have [ a different product, ] but my CIO wants
the ability to inspect someone's mail from home, or on the road. How
does GWSK help? Can they coexist?
A: A CIO, IT Director, or similar technical executive will need to respond
to "emergency" requests from executive management. Even if you have
a robust compliance and audit system in place, it is normally not accessible
remotely, or might not run on the systems available: e.g. a Mac. GWSK
provides this services from any platform, and from any location. GWSK
can be used even if you already have another Trusted Application installed.
Since GWSK does not drop code on your servers, there is no potential
for software conflicts.
Q: Does GWSK work with Groupwise 6.0 and prior?
A: No, the Trusted Application feature of GroupWise was added
in version 6.5. GWSK will only work with a GroupWise 6.5 or 7.0 system.
Q: Will I need to do anything to GroupWise to use GWSK?
A: Yes, you will need to ensure the target e-mail account is accessible
via IMAP. You will need to have turned on IMAP access via at least
one GWIA or on the user's POA. This is a normal feature of GroupWise
and does not constitute a "hack."
Q: How secure is GWSK?
A: The Trusted Application Key used by GWSK is a 64 byte key, generated
by you, which must be presented in conjunction with an application name.
Neither of these can be inferred or derived by non privileged users, and
the application key can only be created, deleted by a GroupWise administrator.
The ability to create and use these keys is already present in your existing
GroupWise system. The key must be provided to GWSK every time you
start the GWSK Proxy, it does not persist this key in any form. GWSK
also offers IMAP over SSL. If you are especially concerned, and don't
trust even an SSL connection, remote access can be facilitated by VPN as
well, providing another layer of encryption.
Q: How big is this key? Is is easily guessable,
or trivial?
A: The cyphertext of the key is approximately 70 - 80 characters
- too big to be memorized by most people. The Key is generated by
GroupWise API calls and appear to be a bunch of random gibberish.
Q: Won't you know what our key is? How do you protect
them?
A: As mentioned above, once you purchase GWSK,
you generate a key specific
to your site. You can create or delete these keys at any time.
The keys you generate are not communicated by GWSK to www.TrafficShaper.com
staff.
Only you and GroupWise know that the key is. The
value of the key is actually created by your GroupWise system, not GWSK code,
the GWSK Manager merely tells you what the GroupWise generated key is.
GWSK Manager is not capable of network communications. Since GroupWise
generates the key, there is no possibility of reverse engineering of GWSK
yielding some sort of magic key generation algorithm.
Q: Does GWSK support clandestine snooping?
A: Caveats: GWSK can be used for clandestine snooping
when used with a mail client capable of creating an off-line copy of a
mailbox. GWSK also performs basic filtering and modification of actions
that would result in mail deletion or modification of the "Seen" flag.
This conceals the fact that someone read previously unread mail, or "oops!"
on the part of the person reading the mail. Specifically a client that
does not modify FLAGS and uses the PEEK methods for reading messages is the
safest. Thunderbird can be configured to create off line copies of
mailboxes leaving the on-line mailbox unchanged. Provided you never
reconnect to the IMAP server, this off line mailbox can be poked and prodded,
copied and so on without the on-line mailbox ever knowing. This is
NOT something you will want to entrust to non-technical staff, as it is very
easy to accidentally set flags or delete messages - tipping your hand.
Q: Does GWSK support clandestine duplication and subsequent
viewing?
A: Yes. Use of IMAPCopy is also a recommended means to flying
under the radar. Uou can use it to duplicate a users mailbox to an
empty GroupWise account withouth their knowledge. So you would prepare
an empty GroupWise account to use when needed. When executives management
needs to inspect the mail you use GWSK and IMAPCopy to duplicate the accounts
contents. The executive can directly inspect mail in the duplicate
account using the duplicate accounts password and ID via web access or GW
client. With this method you necer actually see the targets mail and
its is safer for use by non-technical executives.
Q: Does GWSK prevent modification of the on-line mailbox?
A: We recently added some minimal level of protection against
modifying flags when viewing on-line mailboxes. This is NOT guranteed
to work perfectly with every mail client and has been specifically tested
with Thunderbird. GWSK will provide minimal protection from modification
of message flags due to reading or copying messages. Use the -stealth
command line option to start GWSKProxy. We fully expect that as the
GWSK project moves forward, from your support, that this will be come much
more bullet proof, enabling non-technical staff to use the GWSKProxy in a
clandestine manner.
Q: Is there a demo? Can I test GWSK?
A: Yes. The demo version of the product lacks the Trusted Application
Authentication capabilities ( essentially hard coded to start with -nogw ).
So for testing you will need to provide a password when prompted by
the IMAP client. However other than this, the demo allows you to test
the usability of the GWSKProxy on your workstations, IMAP clients and GroupWise
IMAP server. You can try the -stealth option to see if that works
to protect your on-line mailbox from being modified while reading mail.
You can also test setting up your IMAP client to create an off-line copy
of a production or test mailbox. Other than the IMAP server asking
for a password, all the rest is the same. Just e-mail us and we'll
send you the demo.
Q: How do YOU recommand we use GWSK?
A: GWSK can be used in a variety of ways. First of all, we recommend
you test the impact of using GWSKProxy on a test account. You will
want to anticipate any problems long before you really need to use the GWSK.
The safest way to secure contents in a clandestine fashon is to create
an off-line copy of the mailbox. You can do this using your executive's
workstation, and once you disable GWSKProxy, your executive can review / print
the mailbox contents from this off line copy. For remote access we
suggest the following process: ahead of time, create an empty GroupWise account
with no visibility. Then you can use GWSKproxy to create the off-line
mailbox, once complete copy the folders / contents to the empty account,
now provide the executive with the login ID and password for the dummy account.
That can be done while both you and the executive are in remote locations.
As a last resort, you can provide the executive with direct access
to the mailbox using GWSKProxy, of course ensure you have tested the -stealth
option with the mail client you intend to use and give them instruction.
As GWSK evolves, the latter will become safer and more practical.
Q: Is GWSK some sort of hack or exploit?
A: No. GWSK is based on Novell published API's for GroupWise.
There are no modifications to your GroupWise agent or client applications.
It is completely a client side technology which uses existing features
built into GroupWise
Q: Does GWSK support IMAP via SSL?
A: Of course. Configure your GroupWise IMAP server to allow SSL
connections as you would normally. Just use the GWSKProxy in SSL
mode. All communications between your workstation and GroupWise will
be encrypted, including your Trusted Application Key. This allows GWSK
to be used securely over the Internet.
Q: Can GWSK be used as a generic SSL proxy for IMAP clients
that do not support SSL?
A: Yes. GWSK can be used as a generic SSL tunnel. But it
is designed specifically for the purpose of facilitating access to GroupWise.
Again, GWSK Proxy is harmless without the trusted application key.
The GWSK Proxy must always present the credentials prior to gaining
access to IMAP.
Q: Can I see address books and rules, and proxy settings?
A: No. GWSK can only see what an IMAP client can see: mail and
calendar items. This is about the only thing you cannot do with GWSK.
If you really, really, really need these you should use another product.
But this limitation is more than made up for by other GWSK features.
Q: Can I delete, empty trash, or perform other operations
on the mailbox?
A: Yes. GWSK implements a IMAP proxy. All operations
you can perform via IMAP using regular authentication you can perform via
GWSK Proxy. This allows you to use GWSK Proxy to surgically remove
contents from a user's mailbox, for example if a message were accidentally
sent to the wrong user.
Q: Can I run GWSK Proxy on a central system or server?
A: No. It
must be run from the workstation that you run
your IMAP client from. You
must not run the GWSK Proxy
component from a server as this could allow an intruder to access your
GroupWise mailboxes.

